Thursday, 27 December 2018
Friday, 14 December 2018
CCNA Cyber Ops in Sahiwal by Cisco Networking Academy Pakistan
CCNA Cybersecurity Operations
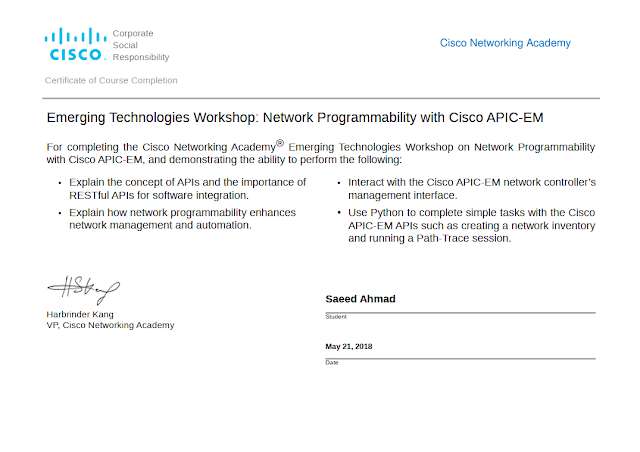
Cyber Security Careers Cybersecurity operations jobs play a key part of securing information systems through the monitoring, detecting, investigating, analyzing, and responding to security events, thus protecting systems from cybersecurity risks, threats, and vulnerabilities. Such jobs are among the fastest-growing roles in IT, as organizations set up security operations centers (SOCs), and establish teams to monitor and respond to security incidents. CCNA Cybersecurity Operations is delivered through the Cisco NetAcad.com learning environment. Instructors can enroll students and teach the course through the same process used for other NetAcad™ courses.
Module Learning Objectives
|
Chapter
1. Cybersecurity and the Security Operations Center
|
●
Explain the role of the Cybersecurity Operations Analyst in the enterprise.
● Explain why networks and data are attacked. ● Explain how to prepare for a career in Cybersecurity operations. |
|
Chapter
2. Windows Operating System
|
●
Explain the Windows Operating System features and characteristics needed to
support cybersecurity analyses.
● Explain the operation of the Windows Operating System. ● Explain how to secure Windows endpoints |
|
Chapter
3. Linux Operating System
|
●
Explain the features and characteristics of the Linux Operating System.
● Perform basic operations in the Linux shell. ● Perform basic Linux administration tasks. |
|
Chapter
4. Network Protocols and Services
|
●
Analyze the operation of network protocols and services.
● Explain how the Ethernet and IP protocols support network communications and operations ● Explain how network services enable network functionality |
|
Chapter
5. Network Infrastructure
|
●
Explain network topologies and the operation of the network infrastructure.
● Explain how network devices enable wired and wireless network communication. ● Explain how devices and services are used to enhance network security. |
|
Chapter
6. Principles of Network Security
|
●
Classify the various types of network attacks.
● Explain how networks are attacked. ● Explain the various types of threats and attacks. |
|
Chapter
7. Network Attacks: A Deeper Look
|
●
Use network monitoring tools to identify attacks against network protocols
and services.
● Explain network traffic monitoring. ● Explain how TCP/IP vulnerabilities enable network attacks. ● Explain how common network applications and services are vulnerable to attack. |
|
Chapter
8. Protecting the Network
|
●
Use various methods to prevent malicious access to computer networks, hosts,
and data.
● Explain approaches to network security defense. ● Use various intelligence sources to locate current security threats. |
|
Chapter
9. Cryptography and the Public Key Infrastructure
|
●
Explain the impacts of cryptography on network security monitoring.
● Use tools to encrypt and decrypt data. ● Explain how the public key infrastructure (PKI) supports network security. |
|
Chapter
10. Endpoint Security and Analysis
|
●
Explain endpoint vulnerabilities and attacks investigation process.
● Use tools to generate a malware analysis report. ● Classify endpoint vulnerability assessment information |
|
Chapter
11. Security Monitoring
|
●
Evaluate network security alerts.
● Explain how security technologies affect security monitoring. ● Explain the types of log files used in security monitoring. |
|
Chapter
12. Intrusion Data Analysis
|
●
Analyze network intrusion data to identify compromised hosts and
vulnerabilities
● Explain how security-related data is collected. ● Analyze intrusion data to determine the source of an attack. |
|
Chapter
13. Incident Response and Handling
|
●
Explain how network security incidents are handled by CSIRTs.
● Apply incident response models, such as NIST 800-61r2 to a security incident. ● Use a set of logs to isolate threat actors and recommend an incident response plan. |
Certification and Careers
|
Address
|
:
|
Career Institute, P-4, 1st Floor, College
Square, Farid Town, Sahiwal, Pakistan
|
|
Mobile
|
:
|
0314-5000083
|
|
Phone
|
:
|
041-2640083
|
|
Email
|
:
|
CCNA in Sahiwal by Cisco Networking Academy Pakistan
CCNA R&S: Introduction to
Networks
CCNA Routing & Switching
Curriculum
Course Overview
- Explain network technologies.
- Explain how devices access local
and remote network resources.
- Describe router hardware.
- Explain how switching operates in
a small to medium-sized business network.
- Design an IP addressing scheme to
provide network connectivity for a small to medium-sized business network.
- Configure initial settings on a
network device.
- Implement basic network
connectivity between devices.
- Configure monitoring tools
available for small to medium-sized business networks.
CCNA Routing & Switching
Curriculum
Course Overview
- Determine how a router will
forward traffic based on the contents of a routing table.
- Explain how switching operates in
a small to medium-sized business network.
- Use monitoring tools and network
management protocols to troubleshoot data networks.
- Configure monitoring tools available
for small to medium-sized business networks.
- Configure initial settings on a
network device.
- Configure Ethernet switch ports.
- Implement VLANs.
- Implement static routing.
- Implement DHCP on a router.
- Implement network address
translation (NAT).
- Implement access control lists
(ACLs) to filter traffic.
CCNA R&S: Scaling Networks
CCNA Routing & Switching
Curriculum
Course Overview
- Configure and troubleshoot
routers and switches
- Resolve common issues with OSPF,
EIGRP, and STP in both IPv4 and IPv6 networks
- Implement a WLAN in a
small-to-medium network
CCNA R&S: Connecting
Networks
CCNA Routing & Switching
Curriculum
Course Overview
- Configure and troubleshoot
network devices
- Resolve common issues with data
link protocols
- Resolve common issues with OSPF,
EIGRP, and STP in both IPv4 and IPv6 networks
- Implement virtual private network
(VPN) operations in a complex network
CCNA R&S 6.0: Bridging
CCNA Routing & Switching
Curriculum
Course Overview
Summary of Additions
- CCNA R&S: Introduction to
Networks now includes extended traceroute activities and more practice in
debugging and network troubleshooting.
- CCNA R&S: Routing and
Switching Essentials has added material related to host routes, device
discovery, NTP, and password recovery.
- CCNA R&S: Scaling Networks
has added VTP, extended VLANS, and DTP. You will also learn more about
troubleshooting multi-VLAN and multi-area OSPF, switch stacking, and how
to implement HSRP.
- CCNA R&S: Connecting Networks
has the most updates with new content in the areas of: WAN topologies, IP
errors, security best practices, quality of service, cloud and
virtualization, and network programming.
Requirements
- No prerequisites
Certification and Careers
 |
| Cisco Expert Level Instructor Award Saeed Ahmad CNAGuru |
Sunday, 9 December 2018
CCNA Cyber Ops in Pakistan Training & Certifications
CCNA Cybersecurity Operations
Today's emboldened cybercriminals are tapping into legitimate online resources. They leach server capacity, steal data, and demand ransoms from online victims whose information they hold hostage. The explosive growth in Internet traffic—driven largely by faster mobile speeds and the proliferation of online devices—works in their favor by helping to expand the attack surface. Facing mounting challenges from cybercrime, cyberespionage, insider threats, and advanced persistent threats, organizations are establishing Security Operations Center (SOC) teams of security professionals who can monitor, detect, and respond rapidly to security incidents before they cause damage.
Gain Career-Ready Cybersecurity Skills
“Demand for cybersecurity professionals is expected to rise to 6 million globally by 2019.” (One Million Cybersecurity Job Openings in 2016, Forbes). You can get ready for this in-demand job market by gaining career-ready cybersecurity knowledge and skills from the CCNA Cybersecurity Operations curriculum. This curriculum provides the first step in acquiring the knowledge and skills needed to work with a SOC team and can be a valuable part of beginning a career in the exciting and growing field of cybersecurity operations. It helps prepare you for entry-level cybersecurity career opportunities and is aligned with the Understanding Cisco Cybersecurity Fundamentals (210-250 SECFND) and Implementing Cisco Cybersecurity Operations (210-255 SECOPS) exams, leading to the Cisco CCNA Cybersecurity Operations certification.
The course provides practical, relevant, and job-ready skills aligned closely with the specific tasks expected of SOC professionals through the following components:
- Interactive, multimedia content
- Activities, virtual hands-on labs, and Packet Tracer activities that reinforce learning
- Links to articles and websites for enhanced learning on specific topics
- Quizzes and exams to check your understanding of the information covered
Cybersecurity Careers
Cybersecurity operations jobs play a key part in securing information systems through the monitoring, detecting, investigating, analyzing, and responding to security events, thus protecting systems from cybersecurity risks, threats, and vulnerabilities. Such jobs are among the fastest-growing roles in IT as organizations set up security operations centers (SOCs) and establish teams to monitor and respond to security incidents. The CCNA Cybersecurity Operations course is delivered through the Cisco NetAcad.com learning environment. Instructors can enroll students and teach the course through the same process used for other NetAcad™ courses.
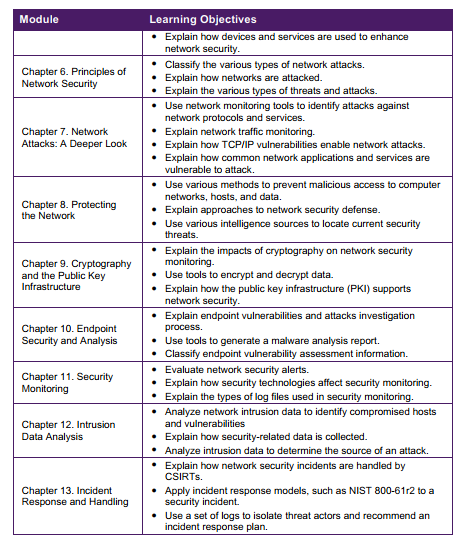
Learning Objectives
Chapter 1: Cybersecurity and the Security Operations Center
- Explain the role of the Cybersecurity Operations Analyst in the enterprise.
- Explain why networks and data are attacked.
- Explain how to prepare for a career in Cybersecurity operations.
Chapter 2: Windows Operating System
- Explain the Windows Operating System features and characteristics needed to support cybersecurity analyses.
- Explain the operation of the Windows Operating System.
- Explain how to secure Windows endpoints.
Chapter 3: Linux Operating System
- Explain the features and characteristics of the Linux Operating System.
- Perform basic operations in the Linux shell.
- Perform basic Linux administration tasks.
Chapter 4: Network Protocols and Services
- Analyze the operation of network protocols and services.
- Explain how the Ethernet and IP protocols support network communications and operations.
- Explain how network services enable network functionality.
Chapter 5: Network Infrastructure
- Explain network topologies and the operation of the network infrastructure.
- Explain how network devices enable wired and wireless network communication.
- Explain how devices and services are used to enhance network security.
Chapter 6: Principles of Network Security
- Classify the various types of network attacks.
- Explain how networks are attacked.
- Explain the various types of threats and attacks.
Chapter 7: Network Attacks: A Deeper Look
- Use network monitoring tools to identify attacks against network protocols and services.
- Explain network traffic monitoring.
- Explain how TCP/IP vulnerabilities enable network attacks.
- Explain how common network applications and services are vulnerable to attack.
Chapter 8: Protecting the Network
- Use various methods to prevent malicious access to computer networks, hosts, and data.
- Explain approaches to network security defense.
- Use various intelligence sources to locate current security threats.
Chapter 9: Cryptography and the Public Key Infrastructure
- Explain the impacts of cryptography on network security monitoring.
- Use tools to encrypt and decrypt data.
- Explain how the public key infrastructure (PKI) supports network security.
Chapter 10: Endpoint Security and Analysis
- Explain endpoint vulnerabilities and attacks investigation process.
- Use tools to generate a malware analysis report.
- Classify endpoint vulnerability assessment information.
Chapter 11: Security Monitoring
- Evaluate network security alerts.
- Explain how security technologies affect security monitoring.
- Explain the types of log files used in security monitoring.
Chapter 12: Intrusion Data Analysis
- Analyze network intrusion data to identify compromised hosts and vulnerabilities.
- Explain how security-related data is collected.
- Analyze intrusion data to determine the source of an attack.
Chapter 13: Incident Response and Handling
- Explain how network security incidents are handled by CSIRTs.
- Apply incident response models, such as NIST 800-61r2 to a security incident.
- Use a set of logs to isolate threat actors and recommend an incident response plan.
Certification and Careers
The CCNA Cybersecurity Operations curriculum prepares you for entry-level security career opportunities in a Security Operations Center, and for the Understanding Cisco Cybersecurity Fundamentals (SECFND) certification exam (210-250) and Implementing Cisco Cybersecurity Operations (SECOPS) certification exam (210-255), leading to the Cisco CCNA Cybersecurity Operations certification.