Your Pathway to CCNAv7 Certification
The Cisco Certified Network Associate (CCNA) v7 curriculum is a comprehensive program designed to equip you with the essential skills for a successful career in the IT industry. The curriculum is divided into three courses that provide a deep dive into networking fundamentals, from basic concepts to advanced enterprise solutions. Upon completion of all three courses, you will be well-prepared to take the Cisco CCNA certification exam.
CCNAv7: Introduction to Networks (ITN)
The first course in the CCNA curriculum, ITN, introduces the foundational concepts of computer networking. You will explore the architecture, models, protocols, and networking elements that connect users, devices, applications, and data across the internet and modern computer networks. The course covers essential topics like IP addressing and the fundamentals of Ethernet. By the end of this course, you will be able to build simple Local Area Networks (LANs), integrate IP addressing schemes, implement foundational network security, and perform basic configurations for routers and switches.
Key Learning Outcomes:
- Explain the advances in modern network technologies.
- Implement initial settings, including passwords and IP addressing, on network switches and end devices.
- Understand how network protocols enable devices to access local and remote network resources.
- Calculate and apply IPv4 and IPv6 subnetting schemes to efficiently segment a network.
- Configure a small network with essential security best practices.
CCNAv7: Switching, Routing, and Wireless Essentials (SRWE)
The second course in the CCNA curriculum focuses on the technologies that support small-to-medium business networks. SRWE delves into switching technologies, router operations, wireless local area networks (WLANs), and security concepts. You will learn key switching and routing concepts and gain hands-on experience in basic network configuration and troubleshooting. The course also covers how to identify and mitigate LAN security threats and how to configure and secure a basic WLAN.
Key Learning Outcomes:
- Configure VLANs and Inter-VLAN routing, applying security best practices.
- Troubleshoot inter-VLAN routing on Layer 3 devices.
- Configure redundancy on a switched network using Spanning Tree Protocol (STP) and EtherChannel.
- Implement dynamic addressing and first-hop redundancy protocols to support available and reliable networks.
- Configure and secure a WLAN using a Wireless LAN Controller (WLC) and Layer 2 security best practices.
CCNAv7: Enterprise Networking, Security, and Automation (ENSA)
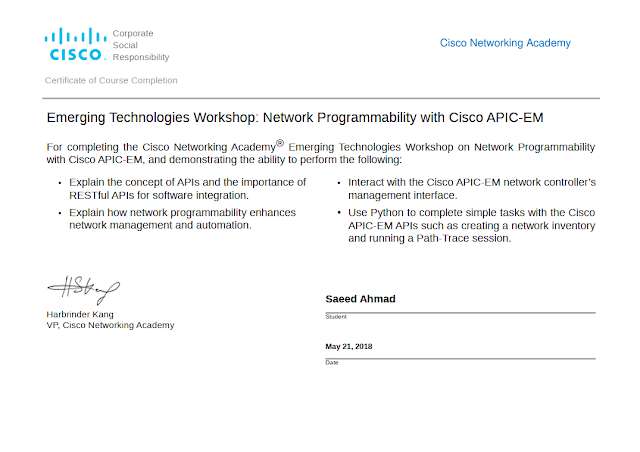
The third and final course in the CCNA curriculum, ENSA, explores the architectures and considerations for designing, securing, operating, and troubleshooting enterprise networks. This course covers wide area network (WAN) technologies, quality of service (QoS) mechanisms for secure remote access, and an introduction to software-defined networking, virtualization, and automation concepts. You will gain the skills to configure and troubleshoot enterprise networks, identify and protect against cybersecurity threats, and use network management tools. The course also introduces controller-based architectures and how Application Programming Interfaces (APIs) enable network automation.
Key Learning Outcomes:
- Configure single-area OSPFv2 in both point-to-point and broadcast multiaccess networks.
- Implement IPv4 Access Control Lists (ACLs) to filter traffic and secure administrative access.
- Configure Network Address Translation (NAT) services on an edge router to provide IPv4 address scalability.
- Understand and explain how VPNs and IPsec secure site-to-site and remote access connectivity.
- Grasp the concepts of network virtualization, software-defined networking, and automation.