Objectives
•Review
OSPF Single Area•Multiarea OSPF
Implementation
•Types
of LSAs Exchanged
Between Areas
•Configuring
Multiarea
OSPFv2 and
OSPFv3
•Verifying
an
OSPFv2 and OSPFv3 Configuration
•Review
OSPF Key Points
OSPF
Single Area - Review
•Link
State Routing Protocol
•Faster
Convergence
•Cost
Metric (Cisco – Bandwidth)
•Identical
Link-State Databases (LSDBs)
•SPF –
Dijkstra’s
Algorithm
•Determine
Neighbors on Directly-connected links
•Use
Link-State Packets (LSP) for each directly-connected link
•Flood
LSPs to neighbors
As a
review, OSPF (Open Shortest Path First) is a Link State Routing Protocol with an
Administrative distance (AD) of 110.
(AD
= trustworthiness
or preference
of the routing protocol.) OSPF
is classless;
therefore, it supports VLSM and CIDR.
•
OSPF
quickly propagates network changes.
Routing
changes
trigger OSPF
routing updates
so it is more efficient than distant vector routing protocols such as RIPv2. (RIPv2
uses periodic
updates of every 30 seconds.)
In
OSPF, The cost of a link is based on
bandwidth only. Higher bandwidths will
have a lower cost.
OSPF
creates and maintains three databases:
•Adjacency
database -
Creates the neighbor table
•Link-state
database (LSDB) -
Creates the topology table
•Forwarding
database -
Creates the routing table
These
tables contain a list of neighboring routers to exchange routing information
with and are kept and maintained in RAM.
Once the network is converged all
routers in an area will have identical link-state databases!
OSPF uses the Shortest Path First algorithm to choose the best path.
The CPU processes the neighbor and topology tables using Dijkstra’s SPF algorithm This
algorithm
is
based on the cumulative cost to reach a destination. The SPF algorithm creates
an SPF tree by placing each router at the root of the tree and calculating the
shortest path to each node. The SPF tree is then used to calculate the best
routes. OSPF places the best routes into the forwarding database, which is used
to make the routing table.
OSPF
uses link-state packets (LSPs) to establish and maintain neighbor adjacencies
and exchange routing updates. LSPs represent the state of a router and its
links to the rest of the network.
 |
| Single Area OSPF |
OSPF
Packet Types
OSPF exchanges messages to convey
routing information using five types of packets. These packets are:
•Hello
packet
•Database
description packet
•Link-state
request packet
•Link-state
update packet
•Link-state
acknowledgment packet
These
packets are used to discover neighboring routers and also to exchange routing
information to maintain accurate information about the network.
 |
| OSPF Packet Type |
OSPF
– Hello Packet
Let’s
look at the Hello Packet
The
OSPF Type 1 packet is the Hello packet. Hello packets are used to:
•Discover
OSPF neighbors and establish neighbor adjacencies.
•Advertise
parameters on which two routers must agree to become neighbors.
•Hello
Packets are also used to Elect the
Designated Router (DR) and Backup Designated Router (BDR) on multiaccess networks like Ethernet and Frame
Relay. Just
a reminder…Point-to-point links
do not require DR or BDR.
The
figure displays the fields contained in the Type 1 Hello packet. Important
fields shown in the figure include:
•Type - Identifies the type of packet. A
one (1) indicates a Hello packet. A value 2 identifies a DBDescription packet, 3 an LSRequest packet, 4 an LSUpdate packet, and 5 an LSAck packet.
•Router
ID - A
32-bit value expressed in dotted decimal notation used to uniquely identify the originating router. (an IPv4
address)
•Area
ID -
Area from which the packet originated.
•Network
Mask -
Subnet mask associated with the sending interface.
•Hello
Interval -
Specifies the frequency, in seconds, at which a router sends Hello packets. The
default Hello interval on multiaccess networks is 10 seconds. This timer
must be the same on neighboring routers; otherwise, an adjacency is not
established.
•Router
Priority -
Used in a DR/BDR election. The default priority for all OSPF routers is 1, but
can be manually altered from 0 to 255. The higher the value, the more likely
the router becomes the DR on the link.
•Dead
Interval - Is
the time in seconds that a router waits to hear from a neighbor before
declaring the neighboring router out of service. By default, the router Dead
Interval is four times the Hello interval. This timer must be the same on
neighboring routers; otherwise, an adjacency is not established.
•Designated
Router (DR) -
Router ID of the DR.
•Backup
Designated Router (BDR) -
Router ID of the BDR.
•List
of Neighbors -
List that identifies the router IDs of all adjacent routers.
OSPF
– Link State Updates (LSU)
•Type
4: Link-State Update (LSU) packet -
Used to reply to LSRequests (type 3) and to announce new
information. LSUs can be one of 11 different types of
LSAs. LSUs are sometimes referred to as LSAs. Only the first 5 LSA types are
covered on the CCNA.
Basic
OSPF Configuration
R1(config)#int fa 0/0
R1(config-if)#ip
address 172.16.1.17 255.255.255.240
R1(config)#int s
0/0/0
R1(config-if)#ip
address 192.168.10.1 255.255.255.252
R1(config)#int s
0/0/1
R1(config-if)#ip
address 192.168.10.5 255.255.255.252
R1(config-if)#router
ospf 1
R1(config-router)#network
172.16.1.16 0.0.0.15 area 0
R1(config-router)#network
192.168.10.0 0.0.0.3 area 0
R1(config-router)#network
192.168.10.4 0.0.0.3 area 0
 |
| OSPF Diagram configuration |
This
is a basic single area OSPF configuration
Interfaces
are configured and then networks are advertised. The wildcard mask is used to identify which
bits in the network address are significant.
The network 172.16.1.16/28 will be advertised as 172.16.1.16 0.0.0.15.
This wildcard mask is the inverse of the subnet mask, 255.255.255.240. Notice the subnet mask for /30 is
255.255.255.252 and the wildcard mask used to advertise this network is
0.0.0.3. (255.255.255.255 –
255.255.255.252 = 0.0.0.3)
OSPF
Router ID
1.Use the
IP address configured with the OSPF router-id command.
2.If the
router-id is not configured, the router chooses highest IP address of any of
its loopback interfaces.
3.If no
loopback interfaces are configured, the router chooses highest active IP
address of any of its physical interfaces.
Every
router requires a router ID to participate in an OSPF domain. The router ID can
be defined by an administrator or automatically assigned by the router.
The
router ID is used by the OSPF-enabled router to:
•Uniquely
identify the router
•Participate
in the election of the
DR and BDR
Let’s
review how to determine the router ID? As illustrated in the
figure, Cisco routers derive the router ID based on one of three criteria, in
the following order:
1.The
router ID is configured
using
the OSPF router-id rid router configuration mode command.
The rid value is any 32-bit value expressed
as an IPv4 address. This is the recommended method to assign a router ID. (Example:
1.1.1.1)
2.If
the router ID is not configured, the router chooses the highest
IPv4 address of any of configured loopback interfaces. This is the next best
alternative to assigning a router ID.
3.If
no loopback interfaces are configured, then the router chooses the highest
active IPv4 address of any of its physical interfaces. This is the least
recommended method because it makes it more difficult for administrators to
distinguish between specific routers.
R1(config)#interface
loopback 0
R1(config-if)#ip
address 10.1.1.1 255.255.255.255
R1(config)#router
ospf 1
R1(config-router)#router-id
10.1.1.1
Reload
or use "clear
ip
ospf
process"
command, for this to take effect
OSPF
Metric - Cost
•Cisco
IOS
uses the cumulative bandwidths of the outgoing interfaces from the router to
the destination network as the cost value
•Cost
for an
interface is calculated as 10 to the 8th power divided by bandwidth in bps
•Results
in interfaces
with a bandwidth of 100 Mbps and higher having the same OSPF cost of 1
•Reference
bandwidth can
be modified to accommodate networks with links faster than 100
Mbps using
the OSPF command auto-cost reference-bandwidth
•OR –
Directly specify the cost for a link:
R1(config)#interface
serial 0/0/0
R1(config-if)#ip ospf cost
1562
 |
| default Cisco OSPF Cost Value |
OSPF
uses cost as a metric. A lower cost indicates a better path than a higher cost. A 10-Mb/s Ethernet line has a higher cost
than a 100-Mb/s Ethernet line.
The formula used to calculate the OSPF
cost is:
•Cost = reference
bandwidth /interface
bandwidth
•The
default reference bandwidth is 10^8 (100,000,000) as you can see in the graphic; therefore, the formula is:
•Cost = 100,000,000
bps / interface
bandwidth in bps
•Refer
to the table for a breakdown of the cost
calculation. Notice that FastEthernet, Gigabit Ethernet, and 10 GigE
interfaces share the same cost, because the OSPF cost value must be an integer.
Consequently, because the default reference bandwidth is set to 100 Mb/s, all
links that are faster than Fast Ethernet also have a cost of 1.
Reference
bandwidth can be modified to accommodate networks with links faster than 100
Mbps using the OSPF command auto-cost reference-bandwidth
The
“auto-cost
reference-bandwidth” command must be configured on every router in the OSPF
domain. The value is expressed in Mb/s; therefore, to adjust the costs for:
•Gigabit
Ethernet - auto-cost
reference-bandwidth 1,000
•10
Gigabit Ethernet - auto-cost
reference-bandwidth 10,000
•To
return to the default reference bandwidth, use the auto-cost
reference-bandwidth 100 command.
As
seen in the last bullet, you
do
have the choice to define the cost that will be used in OSPF calculations with the interface command, ip ospf cost.
OSPF
and Multiaccess
Networks
•Link-state
routers
flood their link-state packets when OSPF is initialized or when there is a
change in the topology.
•In a multiaccess
network this flooding can become excessive.
•On multiaccess
networks, OSPF elects a Designated Router (DR) and a Backup Designated
Router (BDR) in
case
the Designated Router fails.
•All
other routers become DROthers
•DROthers only
form full adjacencies with the DR and BDR in the network, and send their LSAs
to the DR and BDR using the multicast address 224.0.0.6 (IPv6 FF02::06)
•The
solution to managing the number of adjacencies and the flooding of LSAs on a multiaccess network is the DR. On multiaccess networks such as
ethernet or
frame relay, OSPF elects a DR to be the
collection and distribution point for LSAs sent and received. A BDR is also
elected in case the DR fails. All other routers become DROTHERs. A DROTHER is a
router that is neither the DR nor the BDR.
•DROthers only form full adjacencies with
the DR and BDR in the network, and send their LSAs to the DR and BDR using the
OSPF multicast address 224.0.0.6 (IPv6
FF02::06)
Why
Multiarea
OSPF?
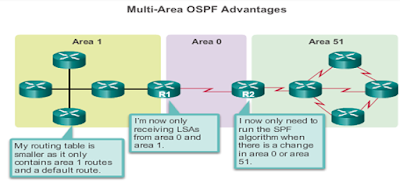
Here
we have an implementation of Multi-Area OSPF with 3 areas, area 1, area 0, and
area 51. The result is smaller routing
tables and less LSAs. SPF is only run
within an area if there is a change in the network.
OSPF
Two-Layer Area Hierarchy
Multiarea OSPF
is implemented in a two-layer area
hierarchy:
Backbone
(Transit)
area -
•Area
whose primary function is the fast and efficient movement of IP packets.
•Interconnect
with other OSPF area types
•Called
OSPF area 0 which all other areas directly connect
Regular
(Non-backbone)
area -
•Connects
users
and resources
•A regular
area does not allow traffic from another area to use its links to reach other areas
Multiarea OSPF is implemented in a two-layer
area hierarchy:
•Backbone
(Transit) area -
Hierarchical networking defines the backbone
area
or area 0 as the core to which all other areas directly connect. Backbone areas
interconnect with other OSPF area types. An OSPF backbone area’s primary function is the fast and
efficient movement of IP packets. Generally, end users are not found within a
backbone area.
•Regular
(Non -backbone)
area -Connects
users and resources. Regular areas are usually set up along functional or
geographical groupings. By default, a regular area does not allow traffic from
another area to use its links to reach other areas. All traffic from other
areas cross area 0.
Types
of OSPF Routers
There
are four different types of OSPF routers:
•Internal
router –
This is a router that has all of its interfaces in the same area. All internal
routers in an area have identical LSDBs.
•Backbone
router –
This is a router in the backbone area. Generally, the backbone area is set to
area 0.
•Area
Border Router (ABR) – This is a router that has
interfaces attached to multiple areas. It must maintain separate LSDBs for each
area it is connected to, and can route between areas. ABRs are exit points for
the area, which means that routing information destined for another area can
get there only via the ABR of the local area. ABRs can be configured to
summarize the routing information from the LSDBs of their attached areas. ABRs
distribute the routing information into the backbone. The backbone routers then
forward the information to the other ABRs. In a multiarea network, an area can have one or more
ABRs.
•Autonomous
System Boundary Router (ASBR) –
This is a router that has at least one interface attached to an external
internetwork (another autonomous system), such as a non-OSPF network. An ASBR
can import non-OSPF network information to the OSPF network, and vice versa,
using a process called route redistribution.
•Redistribution
in multiarea OSPF occurs when an ASBR connects
different routing domains (e.g., EIGRP and OSPF) and configures them to
exchange and advertise routing information between those routing domains.
•A
router can be classified as more than one router type. For example, if a router
connects to area 0 and area 1,
it
falls under two different classifications: a
backbone router, and
an ABR.